In this post, we've seen how WPS can be exploited to hack WiFi networks. The tools we used are in our Top 5 WiFi Hacking Tools! To protect yourself, your best chance is to turn off WPS from your router's page. If you don't wanna do that, upgrade your router's firmware to the latest version or buy a newer router if you have an old one. If you want to know how to hack WiFi access point – just read this step by step aircrack-ng tutorial, run the verified commands and hack WiFi password easily. With the help a these commands you will be able to hack WiFi AP (access points) that use WPA/WPA2-PSK (pre-shared key) encryption.


Hardware components | |||||
| × | 1 | |||
| × | 1 | |||
Software apps and online services | |||||
| |||||
Hand tools and fabrication machines | |||||
| |||||
Story
1. Project Presentation
Wi-Fi Hacking Drone: Is a drone with a SBC (UDOO) on board. When flying, it scans Wi-Fi signal and try to hack the password of the router found, otherwise, if it's impossible to hack, the UDOO save only the packet that contains the handshake to allow to finish work on the ground.
2. Needed parts
- UDOO Quad

- Wi-Fi adapter (Ubuntu Compatible)
- Aircrack-ng
3. Proceedings
3.1 Aircrack-ng Installation
For using Aircrack-ng on Linux distribution, we have to install it. Usually it is available on any packet manager but in our project we have to install the version for ARM processor that isn't available on packet manager.
Airjack Wifi Hack Download
To install it follow this lines:
3.2 How to utilize Aircrack-ng
In this part I want to describe how to utilize Aircrack to collect the handshake and crack the Wi-Fi. So now you can mount your UDOO into your drone and connect it to your via SSH and the secondary Wi-Fi adapter.
This command will enable the virtual interface wlan0, you need to configure the card in monitor mode, i.e., mon0.
Now we can turn off the interface mon0 to change later MAC address.
Through this command MAC address of our platform UDOO we will be changed at our discretion.
With the above command is detected mon0 interface with the new MAC.
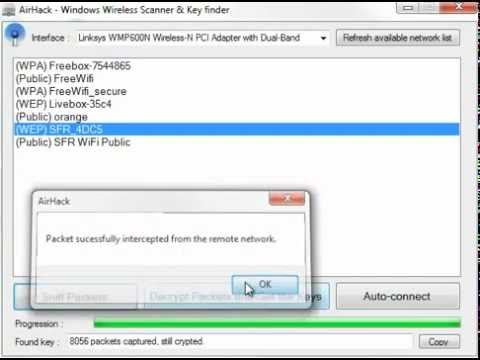
Airjack Wifi Hacked
We can then look for Wi-Fi signals in the vicinity.
Once you choose the Wi-Fi to Hacking, ignore the negative channels and depending on channel served by the Wi-Fi choose the channel number (in this case 6), we put the bssid the network that will associate a file that will serve later for the handshake, and finally we give the interface to which to refer.
This step sends a message to the wireless client saying that is no longer associated with the network. The wireless client will then re-authenticate again with the network. The re-authentication is what generates the authentication handshake we are interested in collecting. This is what we use to break the WPA/WPA2 pre-shared key.
The purpose of this phase is to actually break the WPA/WPA2 pre-shared key. To do this, you need a dictionary of words as input. Basically, Aircrack-ng takes each word to see if this is actually the pre-shared key.
Read moreCredits
Marco Mancini
Airjack Wifi Hacks
If you are unable to Hack WPA / WPA2 WiFi network using WPS Feature, then you have to crack actual WPA / WPA2 encryption. In this hacking process, handshake packets are the only packets which helps in cracking the network. They contain data that can be used to check that WiFi password / key is valid or not. Handshake packets are the 4 packets, which are communicated between the client and the router, when the client connects to the network. These handshake packets can be used to crack WPA / WPA2 key.
Steps to Hack WPA / WPA2 WiFi Network using Word List Attack
Airjack Wifi Hacker
Enable Monitor Mode of Wireless Interface Card.
Capture handshake packets using airodump-ng in Kali Linuxagainst your target network and store the data in a file called hack_wpa_handshake.
Now wait for the handshake packets to be captured. Handshake packets will only be sent when a new client is connected to the network. So, wait until new client is connected to the network.
OR
Alternatively you can use De-authentication Attack, where existing client is disconnected from the network and that client will automatically try to connect to the network again. Once that client is re-connected, handshake packets will be send in the air and then we can capture those handshake packets.
Once the new client is connected to the network or the existing client is disconnected and reconnected to the network, we will receive WPA handshake which is stored in a file called hack_wpa_handshake
Create a word list that contains the large number of passwords / keys
.
Once we have a handshake packet, we will create a word list document that contains password. This document is created usingcrunchtool.Go through the passwords in word list document one by one and use them with the handshake to check that whether password in the document is valid or not.
Use handshake packets to crack WPA/WPA2 password
For cracking WPA/WPA2 password, we will use tool named aircrack-ng. Aircrack-ng will unpack the handshake packet and will match the wordlist passwords one by one with the handshake packet.
There are multiple ways to crack WPA/WPA2 passwords using wordlist attack. Some save the cracking progress and some does not save the cracking progress.
Use aircrack-ng to run wordlist attack to crack WPA/WPA2 passwords without saving cracking progress
In the above command:
- aircrack-ngis the name of the program
- hack_wpa_handshake-01.capis the handshake file which we captured before
- -w PasswordList.txtis the name of my word list document, which contains large number of passwords
aircrack-ng tool runs through the word list document, match each word in the word list with the handshake packet one by one. And at the end, we are able to find the key “abc12345” which is our WiFi network key
For big word list documents, it may takes many hours / days to try all the possible passwords. There could be much bigger dictionaries, that can take many many days to crack the passwords. If we quit aircrack-ng during the process and run the command again, it will lose the session and will start the cracking session from scratch.Save cracking progress while cracking WPA/WPA2 passwords using John the Ripper
In this attack, we will save the cracking session while running aircrack-ng command. So, if we quit aircrack-ng and come back after some time then our session will still be there and we can start the session from where we left. We can save our cracking session usingpassword cracking tool named john the ripper
Here
- johnis the name of the password cracking tool
- –wordlist=PasswordList.txtis the name of the wordlist, which is stored in our current working directory
- –stdoutdisplay this wordlist on the terminal screen
- –session=hackrouter will store the session of john the ripper. Session name is hackrouter
- |using this pipe character (vertical bar), we will redirect the wordlist output and use it as an input to aircrack-ng
- -w – , in this -w attribute, we normally gives the wordlist document name but this time we will use the output generated by john command. And this can be done by using just the – (dash) instead of the wordlist document name
- -b 62:23:6A:96:69:73is the MAC address of my target network
- hack_wpa_handshake-01.capis the name of the handshake file
When john the rippercommand run, it will read all the passwords from a file PasswordList.txt, it will pipe them into aircrack-ng . Aircrack-ng will read these passwords and start cracking. Then when we exit at the middle, john the ripper will store this session in a file named hackrouter.
Now next step is to resume the session using this command
In the above command, we are telling john the ripper to restore the session from where it left last time. And this is stored in a session named hackrouter. This method allows you to stop the attack and start the attack whenever you want.